Configuration
SQLBench Agent Configurations.
Service Account
The SQLBench Agent service account is used to run the SQLBench Agent Windows Service.
It is also used for:
Windows Authentication to SQL Server Instances
If you configure the connection properties of a SQL Server instance to use "Windows Authentication", the SQLBench Agent service account will be used to make that connection.
In this use case a login should be created on the SQL Server instance of "Windows Login" type, and assign the required minimum permissions to that login.
Collecting host telemetry from Windows Hosts
When monitoring a SQL Server instance installed on a Windows host, the SQLBench Agent collects host telemetry (CPU, Memory, Disk utilization etc) using the SQLBench Agent service account.
In this use case the SQLBench Agent service account should be added to the Windows Performance Monitor Users group on the target host.
Do not add the SQLBench Agent service to the Windows Administrators group on the target host.
A Windows domain account should ideally be used as the SQLBench Agent service account, but matching credentials can also be used where a domain is not available.
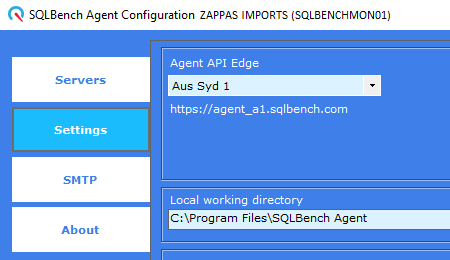
Select an API edge
You can choose which endpoint in our global API network ("Edge") a SQLBench Agent will post its captured telemetry to.
When first activating a SQLBench Agent, you will be prompted to select an endpoint when generating an activation key.
This "activation endpoint" will be used to activate the SQLBench Agent, but you can change it to another endpoint later if you prefer, via the SQLBench Agent settings.
Working Directory
The SQLBench Agent Working Directory is used to cache telemetry captured from monitored SQL Server instances and their hosts before being POSTed to our API, as well as activity logging and exception reporting.
This directory should not be located on the system volume, as the volume of data cached in this directory can vary significantly.
We strongly recommend provisioning a dedicated volume in the SQLBench Agent host to host this direcotry (eg D:\SQLBench\) to avoid filling the system volume.
The SQLBench Agent's service account should also be assigned ownership of this folder so that it can read, write, create & delete files & folders within it.
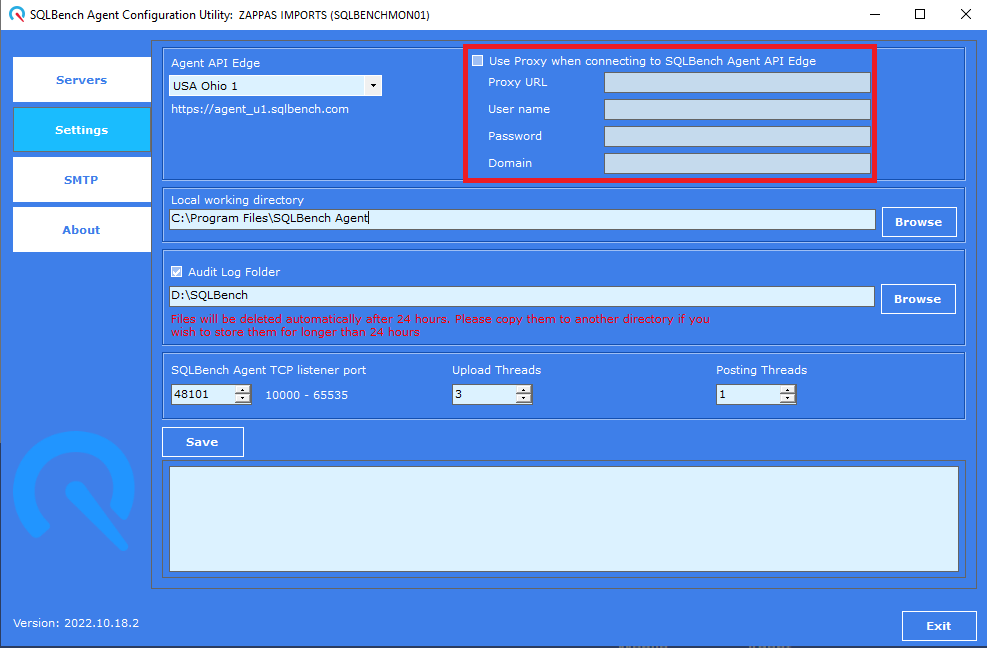
Network Proxy
If the SQLBench Agent service account cannot be directly granted internet access and a proxy account needs to be used, configure a proxy account to be used via the SQLBench Agent > Settings page.
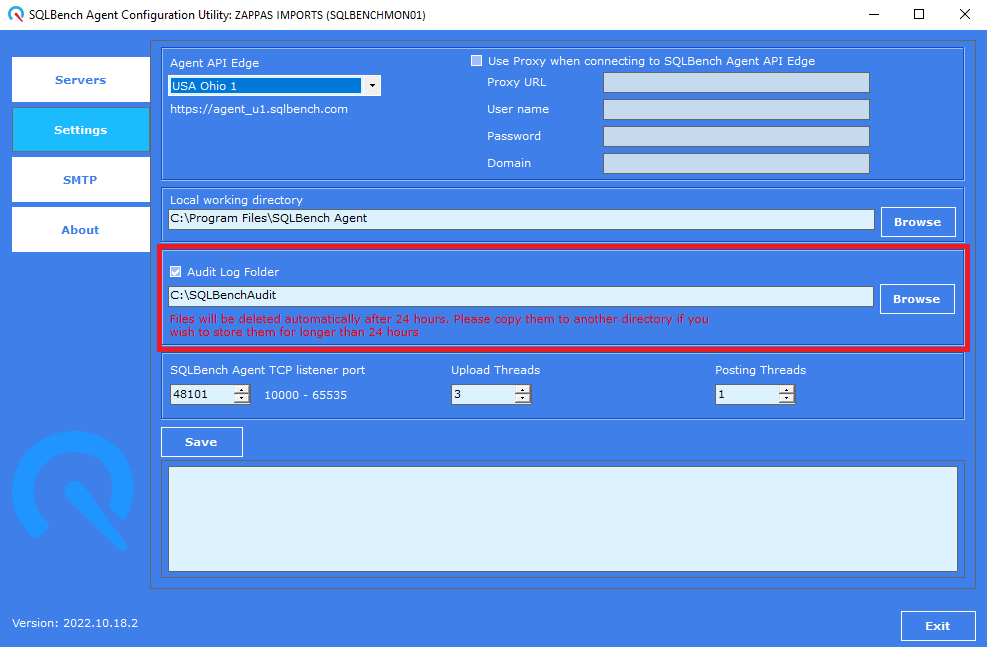
Auditing
SQLBench's audit feature create a copy of all data uploaded to our API to a local folder.
Audit files are retained for 24 hours before being automatically deleted by the agent.
Should you wish to retain audit files for longer, copy them to another directory.
More information about our Auditing feature is available here.
Agent Listener Port
The SQLBench Agent configuration GUI connects to the SQLBench Agent using a local listener port, to perform configuration actions using the SQLBench Agent's permission context rather than that of the user who launched the configuration utility.
The default listener port is 48101, but you can change this port in the SQLBench Agent > Settings page.
 Support
Support